Discover How to Unlock Django Framework With Kerberos

Problem statement:
When we develop applications in Django rest framework we make use of auth-mechanisms, presumably based on django.contrib.auth. Now when an enterprise having an existing identity management solution plans to deploy the application they often mandate that for a seamless user experience, we have a solution that can allow the enterprises to retain their auth mechanism and add on apps leveraging from it. These enterprises use auth mechanisms like Kerberos, LDAP, GSSAPI etc.
Kerberos is used for authenticating users who wish to access services on various servers in an enterprise network. Typically, this is used within corporate/internal environments. Perhaps you want to access your internal payroll site. Rather than re-entering your user/password credentials, your ticket (cached on your system) is used to authenticate allowing for single sign-on.
Basically, Kerberos comes down to just this:
- a protocol for authentication
- uses tickets to authenticate
- avoids storing passwords locally or sending them over the internet
- involves a trusted 3rd-party
- built on symmetric-key cryptography
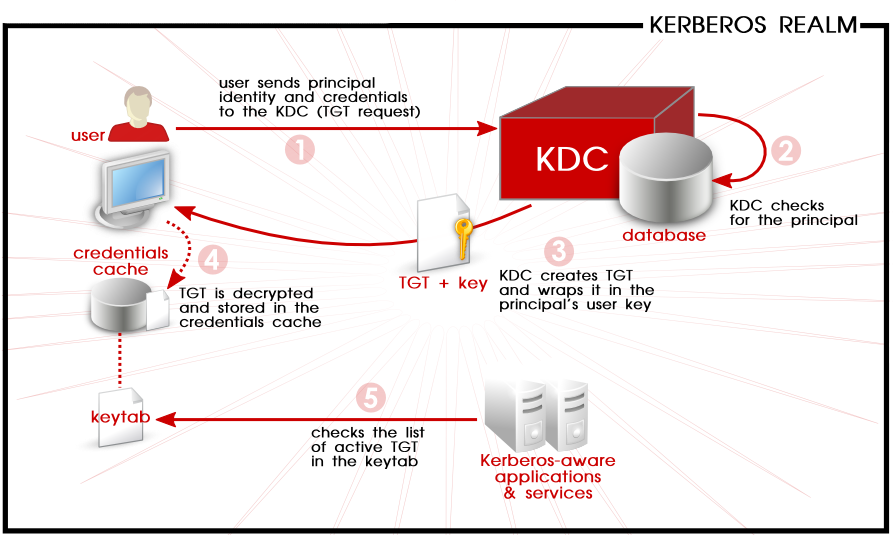
Kerberos terminology:
Client : An entity on the network (a user, a host, or an application) that can receive a ticket from Kerberos.
Ticket : A temporary set of credentials that verify the identity of a client for a particular service.
Realm : A network that uses Kerberos, composed of one or more servers and a potentially large number of clients.
Principal : The principal name or principal is the unique name of a user or service allowed to authenticate using Kerberos.
Kinit : The kinit command allows a principal who has already logged in to obtain and cache the initial ticket
Ticket Granting Service (TGS) : A server that issues tickets for a desired service which are in turn given to users for access to the service. The TGS usually runs on the same host as the KDC
Key Distribution Center (KDC) : A service that issues Kerberos tickets, usually run on the same host as the Ticket Granting Server
Ticket Granting Ticket (TGT) : A special ticket that allows the client to obtain additional tickets without applying for them from the KDC.
Deploying our application on such systems that have an auth-mechanism pre-configured, implies that our application’s auth mechanism must talk to that of the system’s.
Proposed solutions:
A well suited library for Kerberos authentication in Django is “django-auth-kerberos”. It is timely maintained and easy to use and install. It can be installed by following the below steps:
1) pip install django-auth-kerberos
2) following settings are configured in settings.py:
a) Add django_auth_kerberos to the installed apps.
‘Django_auth_kerberos’,
)
b) Set the following parameters:
KRB5_REALM = ‘EXAMPLE.COM’
KRB5_SERVICE = ‘[hostname]/EXAMPLE.COM’# Enabled KDC verification defending against rogue KDC responses
# by validating the ticket against the local keytab.
KRB5_VERIFY_KDC = True# Enable case-sensitive matching between Kerberos and database user names
KRB5_USERNAME_MATCH_IEXACT = True# redirect url after login
LOGIN_REDIRECT_URL = ‘/’# enable kerberos auth backends
AUTHENTICATION_BACKENDS = (
‘django_auth_kerberos.backends.KrbBackend’,
)
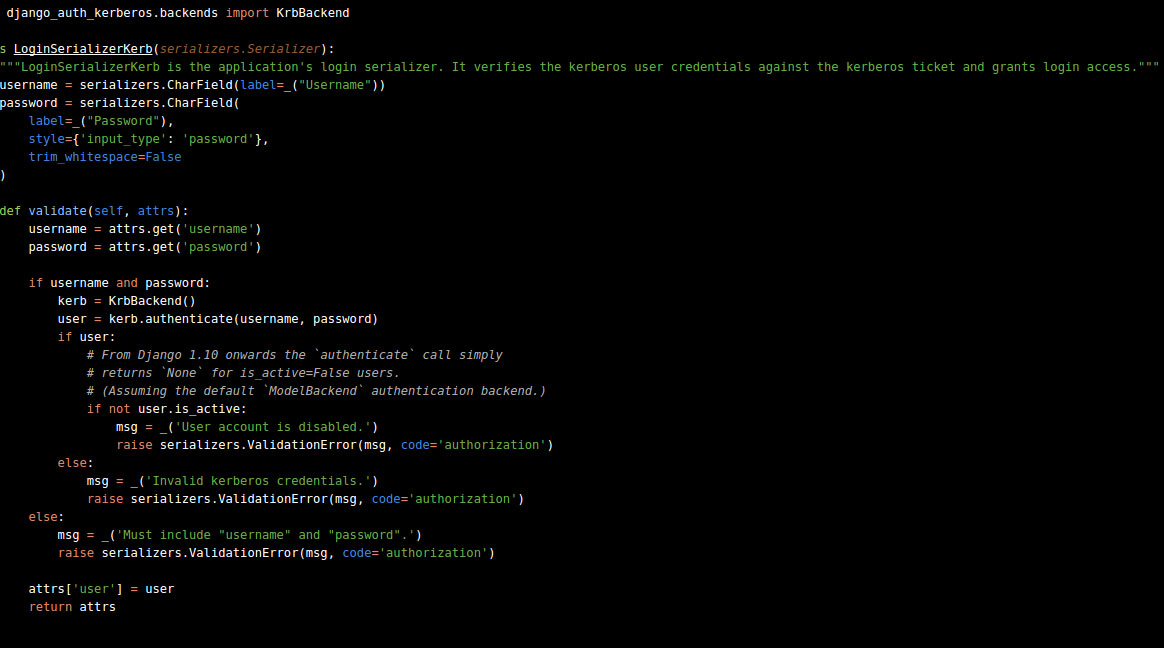
3) KrbBackend is the class responsible for authenticating the user. Here is a snippet of how it can be used:
There are some common errors that one may encounter when authenticating a kerberos user such as the following :
1) “No such file or directory”
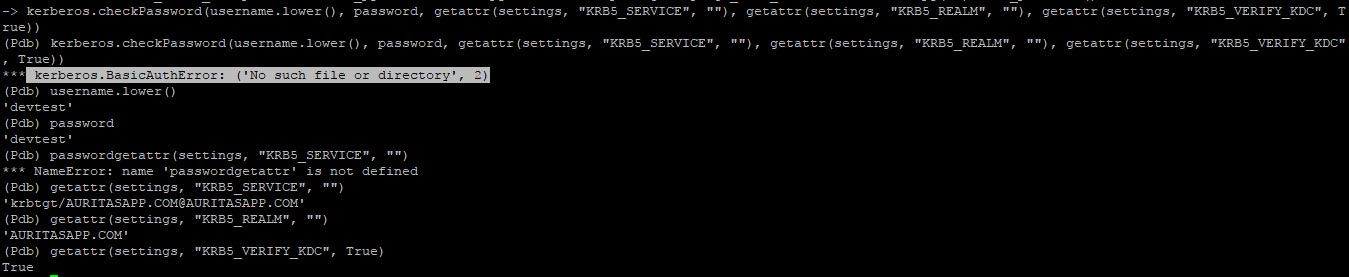
Resolution : Configure an empty service principle. So KRB5_SERVICE should be ‘’.
2) “Permission denied”
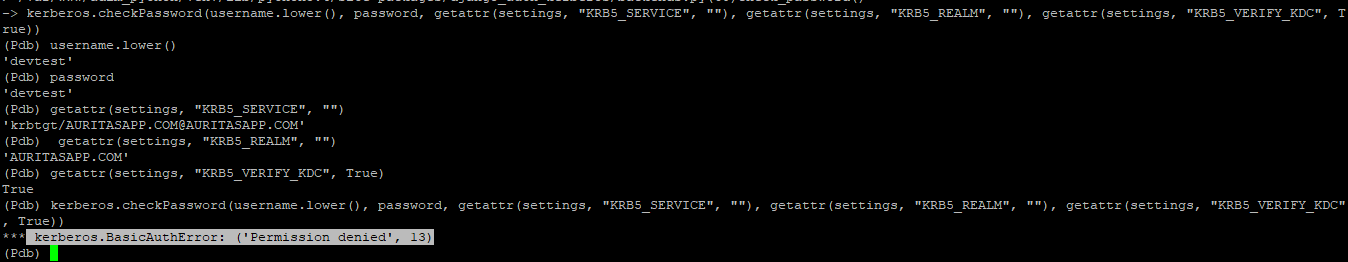
Resolution : Set the value of KRB5_VERIFY_KDC to False.
There are other authentication mechanisms like LDAP (Lightweight Directory Access Protocol) . Usually,Kerberos is used for user authentication and LDAP for user authorization. Even though LDAP can also be used for authentication, Kerberos is prefered since it is more secure.
Both of these mechanisms talk to a directory services database called an Active directory. Active Directory (AD) is a Windows OS directory service that facilitates working with interconnected, complex and different network resources in a unified manner. So in short Kerberos and LDAP are application protocols used to query and modify items in directory services like Active directory.
Why use Django and Kerberos ?
Python and Django provide a number of libraries to authenticate against Kerberos. For instance django-auth-kerberos, django-kerberos, python-kerberos, pykerberos. Using Django allauth on the top of kerberos can server as a double layer of security for the users. Kerberos in itself is a very strong security mechanism. It has:
- Strong mutual authentication. Secrets are not transmitted across the network. Critical authentication data is encrypted. The client (normally a user) is authenticated to the server and the server is authenticated to the client. The client identity is used to authorize services on the server. The server identity prevents the spoofing and hijacking of services.
- Single sign-on. A user convenience meaning a single identity and password can be used across multiple kerberised systems with only one login sequence.
We at Systango provide enterprise-grade Python web development services. To get detailed info, connect with our team for a free consultation here.






