Approaching Web3 From A Security Perspective- Your One-Stop Guide
Published on 08 Dec 2022

Approaching Web3 From A Security Perspective- Your One-Stop Guide
According to a recent study by Web3 security firm Beosin, over $718 million were lost to Web 3-related schemes during the second quarter of 2022. Are you curious to learn about the security perspectives of Web3? We have it all in this one-stop guide on Web3 and its security.
The internet and digital technologies related to it keep changing quite fast. The concept of the web and online services and technologies has evolved rapidly over the decades. The days of static web pages rendering at a snail’s pace on PCs powered by dial-up internet connections seem archaic.
Nowadays, people access the web on blazing-fast 4G and 5G wireless networks, on the move. The world is on the threshold of entering Web 3.0.
Web3 can be defined as an enhanced and evolving iteration of the Internet. It is going to be decentralized, and users will be able to avail a secure P2P network without relying on third parties much.
The Transition From Web 2.0 To Web 3.0 – A Major Game-Changer
From the static and limited version of the internet, prevalent in the 1990s, people made a quick transition to Web 2.0, which introduced interactivity, video content, social media, etc in their lives.
However, moving from Web2 to Web3 is not going to be as smooth. Decentralization will be the key factor here. It is kind of a double-edged sword. It will offer web users enhanced and faster access to diverse types of online content. But at the same time, decentralization will reduce control over media and intellectual property rights. In a way it is going to be amazing for the end users but for stakeholders will be keeping their authority at stake.
Basics of Web3
With Web3, internet users get more flexibility and freedom. They not only get more interaction scopes with web content but they can evade relying on intermediate entities. Technically speaking, the Web3 ecosystem is reliant on Blockchain technology, which has emerged as the de facto choice of people seeking alternative use of their investment.
The usage of Blockchain in development technology eradicates the need to rely on third-party service providers, including financial intermediaries, the government, etc. It also ensures safe data storage and user anonymity.
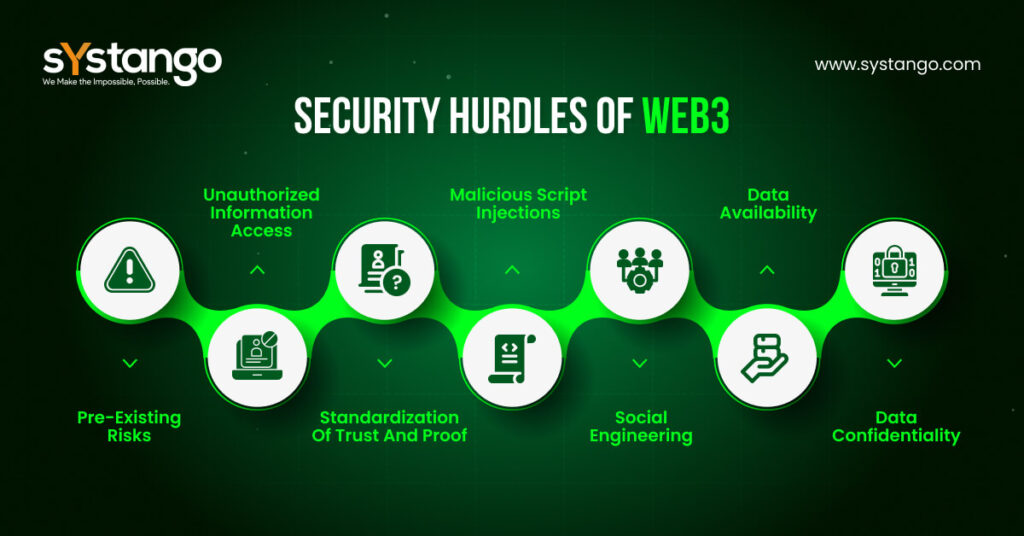
A Glimpse At The Inherent Security Challenges Of Web3
The underlying cryptographic framework of Web3 ensures its safety. However, the reality is there exist certain security loopholes in its infrastructure, and those need to be addressed well. This is largely owing to the pitfalls of the Blockchain sector.
Many Blockchain development approaches have been subjected to stealthy hacking attacks in the last few years. The pseudo-anonymous nature of Web3 platforms makes it hard to fathom the hackers and miscreants.
The defences of Blockchain technology are there, but the numerous attack vectors do exist, too. There are smart contract exploits as well as social engineering attacks and scams. The examples of phishing threats are hard to overlook.
Listed below are the major security hurdles of Web3:
- Data Confidentiality– With Web3, accessing and retrieving data remotely will become easier, but this may also pave the way to lower data confidentiality. With Ai tech being incorporated for data access and retrieval, the risk of data getting shared and breached also goes up.
- Data Quality- Experts assume the reliance on machine-managed data in Web3 can also affect data quality to an extent. Will ML be able to check data for quality like humans? This is one arena that remains under the shroud.
- Hacks and Financial Exploits- Cryptographic technology used in the Blockchain system is deemed to be very safe. However, the reality is hackers have managed to breach safety on several occasions. There are risks of unexpected and unforeseen system glitches, and those can lead to monetary losses.
- Absence of Safety Nets- The Blockchain landscape remains essentially unregulated, and the same can be said about any framework or technology based on it. While laws are being framed in many countries to bring the sector within the legal ambit, the process will still take a long time to be globally accepted. The absence of any safety net or regulation enhances the risks of Web3. Owing to the pseudonymous nature of Web3 applications, tracing the hackers and miscreants can be quite tough.
- Smart Contract Woes- Blockchain proponents say that smart contracts serve as a robust means for enabling data operations. However, the reality is coding flaws do exist in such contracts. Hackers look for such coding loopholes. Even a small disparity in coding paves the way for countless hacks. Several such instances of smart contract hacks have made headlines.
- More Endpoints Accessible to Hackers- With the evolution of the internet, the number of devices used for web access has grown manifold. Now, it is quite commonplace to find 4 to 5 web access devices in a common household. These include laptops, smartphones, and tablets. Wearable devices are gaining traction, and IoT devices are set to become mainstream. What this means is the hackers now have more endpoints and targets to exploit.
Ways To Overcome The Security Hurdles Of Web3
While Web3 is being hailed by technology experts as the upcoming big revolution in the realm of digital tech, there is room for enhancing its numerous security loopholes. The reality is that the Web3 ecosystem is still evolving, and it faces so many security challenges, including some inherited from Web2. Unless the security woes of Web3 are not resolved well, that can lead to serious consequences in the future.
Listed below are the ways using which Web3 applications and setup can be fortified further:
- Implementation and continuation of Web 2.0 security measures– Businesses have been able to evade and thwart many online operation-related hassles through the effective and planned deployment of Web 2.0 security measures. While the evolution of the web will necessitate the deployment of more stringent security measures, using tried and tested security measures will be useful. Web application firewalls are still useful in thwarting a wide range of hacking attacks.
- Extensive code auditing– There is no denying that Web3 is way more complex than its predecessors. Deploying updates on it is going to be more exhaustive. That makes code auditing very important.
- API query encryption- To enhance security on web2.0, a cryptographic protocol named TLS was used. It has to be revamped to ensure the deployment of secure APIs in Web3.
- Real-time monitoring– After a Web3 project has been audited extensively, deploying real-time monitoring measures is also important. The founders have to analyze the project progress, smart contract handling, and things taking place out of the pattern.
- Continuous implementation of emerging safety protocols- As of now, there is not much clarity on Web3-specific safety protocols other than those used for safeguarding Blockchain networks. So, the project providers and the users need to be aware of the safety scene. Deploying the newer safety mechanisms as and when they become available is also necessary.
What Do Web Users Need To Do?
The reality is it is not only the internet technologies that are becoming more sophisticated with time. The hacking groups are also devising newer and more advanced ways to find loopholes in websites and online technology frameworks. The instances of cyber-attacks are becoming refined, fooling even seasoned web users and security experts at times.
Web users, therefore, need to be careful about how they use various online services and platforms. They need to be especially careful about clicking on links and sharing personal data online. It is also prudent to make use of inbuilt security features in devices and applications for accessing Web3 services.
Where Does It All Lead To?
There is no denying that Web3 is an evolving technology with vast potential. It is designed to redefine the web user experience for everyone. However, the absence of a comprehensive security strategy to safeguard the framework and the users is yet to be developed and deployed. The safety of decentralized ledgers is there, but loopholes need to be fixed. Both the Web3 project and framework development entities and users need to know about the proper safety protocols. Deploying the latest online safety mechanism is a necessity, and the same can be said about making secure decisions.
Existing online safety solutions need not be discarded to boost the security of Web3. The existing safety technologies and protocols can be tweaked to address the growing safety needs of Web3. At the same time, newer security protocols have to be made adaptable to cope with the evolving threat landscape. The deployment of AI and ML technologies will go a long way in making the Web3 ecosystem versatile, flexible, and reliable.
Are you looking to leverage next-gen technologies to enhance your service or product? At Systango, we have the right capability to deliver Web3 build, Fintech or Cloud solutions. Connect with us today!
Related posts
Blockchain
Blockchain Development Services for Enterprises: Unlock Efficiency, Trust, and Real Business Impact
21 May 2025
Blockchain
Web Apps
NFT
App Development
The Ultimate Guide to Hiring Blockchain Developers in 2025: Skills, Costs, and Models
15 Apr 2025
Let’s talk, no strings attached.